Edgeos show vpn configuration
I'm clearly missing something, but I want to check all the Phase 1 and Phase 2 settings in the VPN config we have in place-is there a way to do it via GUI, or is the tree the only place. And via CLI I wasn't finding the right commands (I kept getting incomplete commands, but I wasn't sure what I was supposed to be trying).
In the previous section we did not enable the rules manually:
Take a look at ZeroTier, it will save you a lot of time and is arguably more secure than a traditional VPN since it does not demand that you have any presence on the internet as a connection point for clients.
A relative of the owner, who claims to be familiar with VPN connectivity, has managed to get a single VPN connection working, but he now complains that it doesn't appear to support multiple simultaneous connections. I find that hard to believe.
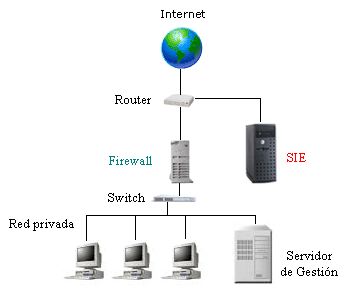
Each campus has a public-facing firewall. When I need to VPN in to fix something, that's the entry point I use. But, what if the problem is the firewall itself? Or with the router or switch directly behind the firewall?
When you say he set up a VPN, is he using the Edgerouter VPN, or another third party? I could see him having issues if he is trying to use some third party crap, but even then the firewall should pass the traffic.
The planned follow up to edgeos show vpn configuration the that will get you 90% of the way there, but is missing a few key pieces of info.
Enter Edge. Each campus has an Edge Lite connected to an ISP. The four of them form a mesh. If you VPN into one of them, you wind up on the management network for that campus. From there, I can L2 directly to all infrastructure devices - no router needed and it bypasses the entry switch.
Robert - 99% of the time I agree with your thought process. However, I never ever open (or allow IMS to open) "back doors". We use a TON of SSL VPN and even allow staff on via BOVPN if they have a device that we will support in their home (we also have a process to install a WatchGuard device in a providers home - at their cost for the hardware).
The planned follow up to the that will get you 90% of the way there, but is missing a few key pieces of info.


Change. That word more than any other defines my career in IT from my start in my high school’s apprenticeship program to most recently being a senior network engineer. I’ve held many roles across desktop support, programming, app admin to storage admin finding each one has helped round out my analytical troubleshooting and design methods.
IPsec VPNs consist of two phases that each uses its own set of hashing/encryption methods called Security Associations (SAs). Phase 1 (P1) is used to authenticate the peers and establish the VPN, whereas the actual data (traffic) is passed in Phase 2 (P2). Because of this, we can define P2 SAs that focus on performance, and P1 SAs that focus on security. The ground rule of any form of encryption/hashing is that an increase in security will (usually) lead to a decrease in performance.
with eth5 (the SFP) for WAN connectivity and local authentication.
You will need to setup a pre-shared secret as a way to protect your VPN from malicious access by running the command set vpn l2tp remote-access ipsec-settings authentication pre-shared-secret "secret phrase"
Komentarze